Using the Dynamic Screening features, MDaemon can track the behavior of sending servers to identify suspicious activity and then respond accordingly. For example, you can temporarily block an IP address from future connections to your server once a specified number of "unknown recipient" errors occur during the mail connection from that IP address. You can also block senders that connect to your server more than a specified number of times in a specified number of minutes, and senders that fail authentication attempts more than a designated number of times.
When a sender is blocked, it is not permanent. The sender's IP address will be blocked for the number of minutes that you have specified on this dialog. Blocked addresses are contained in the DynamicScreen.dat file. It contains a list of the blocked IP addresses and the length of time each will be blocked. This file is memory resident and can be changed from the Advanced button. If you wish to edit or add the IP addresses manually using a text editor, you should create the DynamicScreenUpd.sem Semaphore File and place it in MDaemon's \APP\ folder rather than editing the DynamicScreen.dat file directly.
The "Dynamic screening (WorldClient)" section provides options that allow you to screen WorldClient connections.
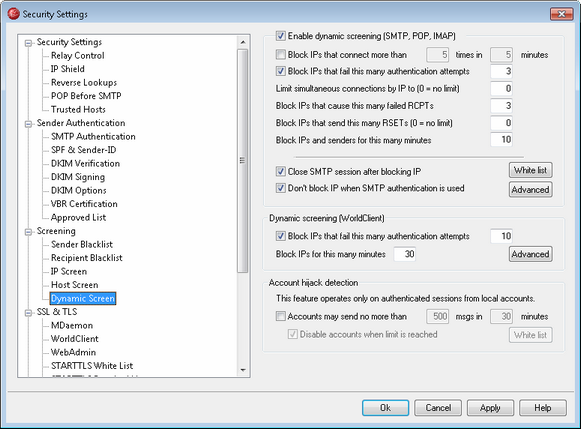
Dynamic Screening
Enable dynamic screening (SMTP, POP, IMAP)
Click this check box to enable dynamic screening. This option screens SMTP, POP3, and IMAP connections.
Block IPs that connect more than [X] times in [X] minutes
Click this check box if you wish to temporarily block IP addresses that connect to your server an excessive number of times in a limited time period. Specify the number of minutes and the number of connections allowed in that period.
Block IPs that fail this many authentication attempts
Use this option if you wish to temporarily block IPs that fail an authentication attempt a specified number of times. This can help prevent attempts to "hack" a user account and falsely authenticate a session. This option monitors SMTP, POP3, and IMAP connections.
Limit simultaneous connections by IP to (0 = no limit)
This is the maximum number of simultaneous connections allowed from a single IP address before it will be blocked. Use "0" if you do not wish to set a limit.
Block IPs that cause this many failed RCPTs
When an IP address causes this number of "Recipient unknown" errors during a mail session it will be automatically blocked for the number of minutes specified in the Block IPs for this many minutes option below. Frequent "Recipient unknown" errors are often a clue that the sender is a spammer, since spammers commonly attempt to send messages to outdated or incorrect addresses.
Block IPs that send this many RSETs (0 = no limit)
Use this option if you wish to block any IP address that issues the designated number of RSET commands. Use "0" if you do not wish to set a limit. There is a similar option on the Servers screen under Default Domains & Servers that can be used to set a hard limit on the allowed number of RSET commands.
Block IPs and senders for this many minutes
When an IP address or sender is automatically blocked, this is the number of minutes the block will last. When the block expires the IP or sender will be able to send to you again normally. This feature prevents you from accidentally blocking a valid IP address or sender permanently.
Close SMTP session after blocking IP
Enabling this option causes MDaemon to close the SMTP session after the IP address is blocked.
Don't block IP when when SMTP authentication is used
Click this checkbox if you want senders who authenticate their mail sessions before sending to be exempt from Dynamic Screening.
White list
Click this button to open the Tarpit/Dynamic Screening white list. IP addresses listed there are exempt from tarpitting and dynamic screening.
Advanced
Click this button to open the DynamicScreen.dat block list. This lists all IP addresses that have been blocked by Dynamic Screening. You can manually add IP addresses and the number of minutes to block them by listing them one entry per line in the form: IP_address<space>Minutes. For example, 192.0.2.0 60.
Dynamic Screening (WorldClient)
Block IPs that fail this many authentication attempts
Use this option if you wish to temporarily block IP addresses that fail a WorldClient authentication attempt a specified number of times. This can help prevent attempts to "hack" a user account and falsely authenticate a session. This option monitors only WorldClient connections.
Block IPs for this many minutes
When an IP address is automatically blocked, this is the number of minutes the block will last. When the block expires the IP address will be able to connect to you again normally. This feature prevents you from accidentally blocking a valid IP address permanently.
Advanced
Click this button to open the Dynamic Screen's WorldClient block list. This lists all IP addresses that have been blocked from connecting to WorldClient. You can manually add IP addresses and the number of minutes to block them by listing them one entry per line in the form: IP_address<space>Minutes. For example, 192.0.2.0 60.
Account Hijack Detection
The options in this section can be used to detect a possibly hijacked MDaemon account and automatically prevent it from sending messages through your server. For example, if a spammer somehow obtained an account's email address and password then this feature could prevent the spammer from using the account to send bulk junk e-mail through your system. You can designate a maximum number of messages that may be sent by an account in a given number of minutes, and optionally cause an account to be disabled if it reaches that limit. There is also a White List that can be used to exempt certain addresses from this restriction.
|
Account Hijack Detection only applies to local accounts over authenticated sessions, and the Postmaster account is automatically exempt. |
Accounts may send no more than [xx] msgs in [xx] minutes
Use this option if you wish to prevent MDaemon accounts from sending more than the specified number of messages in the designated number of minutes. If an account attempts to send more than the allowable number of messages then MDaemon will not drop the connection but it will reject the over-the-limit messages with a 452 error until the time-limit expires. Then it will again accept messages from the account.
Disable accounts when limit is reached
Check this box if you wish to disable accounts that attempt to send more than the allowable number of messages. When this happens, the server sends a 552 error, the connection is dropped, and the account is immediately disabled. The disabled account will no longer be able send mail or check its mail, but MDaemon will still accept incoming mail for the account. Finally, when the account is disabled an email is then sent to the postmaster about the account. If the postmaster wishes to re-enable the account that he can simply reply to the message.
White List
Use the White List to designate any addresses that you wish to exempt from Account Hijack Detection. Wildcards are permitted. For example, "newsletters@example.com" would exempt example.com's "newsletters" MDaemon account, while "*@newsletters.example.com" would exempt all MDaemon accounts belonging to the newsletters.example.com domain. The Postmaster account is automatically exempt from Account Hijack Detection.