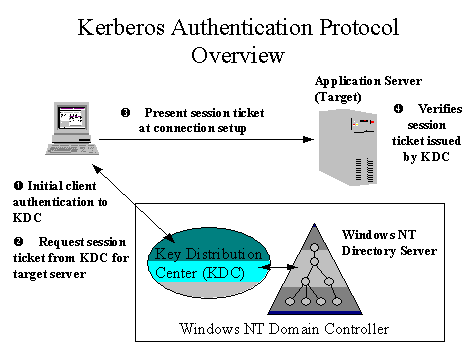
Kerberos is a shared secret authentication protocol because the user and the KDC both know the user's password, or in the case of the KDC, the one-way encrypted password. The Kerberos protocol defines a series of exchanges between clients, the KDC, and servers to obtain and use Kerberos tickets. When a user initiates a log on to Windows NT (and Windows® 95 clients as well) the Kerberos SSP obtains an initial Kerberos ticket (TGT) based on an encrypted hash of the user's password. Windows NT stores the TGT in a ticket cache on the workstation associated with the user's logon context. When a client program attempts to access a network service, the Kerberos run time checks the ticket cache for a valid session ticket to the server. If a ticket is not available, the TGT is sent in a request to the KDC for a session ticket that allows access to the server.
The session ticket is added to the ticket cache and may be reused for future connections to the same server until the ticket expires. The ticket expiration period is defined by domain security policy and is usually set to around eight hours. If the session ticket expires during the middle of an active session, the Kerberos security provider returns appropriate error codes that allow the client and server to refresh the ticket, generate a new session key, and resume the connection.
The following diagram shows the relationship between the client, the KDC, and the application server using the Kerberos authentication protocol.

Figure 5: Kerberos Authentication Protocol Overview
The Kerberos session ticket is presented to the remote service during the initial connection message. Portions of the session ticket are encrypted using a secret key shared between the service and the KDC. The server can quickly authenticate the client by verifying the session ticket without going to the authentication service because the Kerberos run time for the server has a cached copy of the server's secret key. Session connection setup is much faster on the server side than using NTLM authentication. With NTLM, the server would obtain the user credentials and have to reauthenticate the user through the Domain Controller as part of establishing the connection.
Kerberos session tickets contain a unique session key created by the KDC to use for symmetric encryption of authentication information and data transferred between the client and server. In the Kerberos model, the KDC is used as an online trusted third party to generate the session key. Online authentication services are very efficient for distributed application services available in a campus-like network environment.