MTS objects can use the ISecurityProperty interface to obtain security-related information from the object context, including the identity of the client that created the object, as well as the identity of the current calling client. Applications can use this information to implement custom access control, such as using the Win32 security interfaces.
Note Visual Basic programmers can use the SecurityProperty object. The methods for SecurityProperty return user name strings instead of security identifiers (SIDs).
Security Identifiers (SIDs)
A Windows NT security identifier (SID) is a unique value that identifies a user or group. You can use SIDs to determine the exact identity of a user. Because of their uniqueness, SIDs do not have the flexibility of roles.
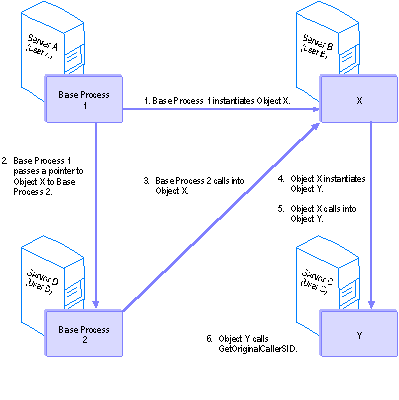
The following figure shows which SIDs are returned by the various methods on ISecurityProperty after a certain sequence of method calls.

Calling the following methods on Object Y returns SIDs associated with these users:
Impersonation
Impersonation allows a thread to execute in a security context different from that of the process that owns the thread. Consider the following application scenario.
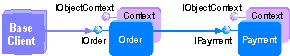
Basic Security Methods described an order-entry scenario in which the base client represents an employee submitting an order. In this scenario, the client is not authorized to use the Payment object and its associated database directly.
Suppose the base client were a report writer for an accounting program. In this case, you want to allow access to the Payment object's database. One way to accomplish this is for the Order object to impersonate the base client, allowing the database to use its own security checking to determine access privileges.
MTS does not promote the use of impersonation, but encourages role-based security. Security is simplified by the single-level of authorization provided by MTS, whereas the impersonation model has an n-level authorization architecture. The report-writer scenario can be simplified by defining a role, such as Accountant, to allow access to the database.