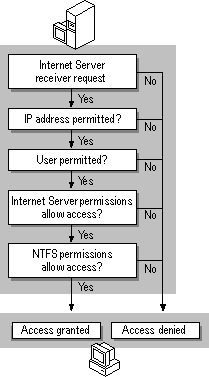
Internet Information Server security builds on the security available with Windows NT Server 4.0. Every connection request that Internet Information Server receives must undergo a rigorous, step-by-step validation process. The Internet Information Server security process is responsible for:
1. Checking the source IP address.
2. Identifying and authenticating Internet users.
3. Assigning logon modes.
4. Allowing access by using NTFS.
Figure 1.1 illustrates how this process works.

Figure 1.1 How Internet Information Server verifies each Internet connection request
In addition, Windows NT Server applications can have Common Gateway Interface (CGI) and ISAPI extensions that require additional logon and password requirements. (For more information on CGI and ISAPI, see "Using ISAPI Security Functions," later in this chapter.)
It is also important to note that each Internet service ¾ WWW, Gopher, and FTP ¾ has different security requirements. When you set up an Internet server, it is best to review which services you plan to provide and to install only those services.
For more installation and configuration information, see the Microsoft Internet Information Server Installation and Administration Guide. For a detailed discussion on Internet security, see Chapter 3, "Server Security on the Internet," in the Microsoft Windows NT Server Resource Kit: Windows NT Server Internet Guide.