Because security in Windows NT is assigned on a per user rather than a per resource basis, a user needs to remember only a single Windows NT user account name and password to log on and use local and network resources. With Windows NT security, all resources and actions are protected by discretionary access control, meaning that some users can be permitted access to a resource or perform an action, while other users can be prevented from accessing the same resource or action. Security is very flexible–for example, different permissions for different users can be set on different files in a directory. Windows NT security applies both to users working at the computer where the resource is located and to users accessing the resource over the network.
For Windows NT, the basic unit of security and centralized administration is the domain. A domain is a collection of computers that recognize a common security accounts database. Four types of computers participate in domain security: primary domain controllers (PDCs), backup domain controllers (BDCs), servers, and workstations.
Each domain has one PDC, which maintains the security accounts database for the domain. A domain can have any number of BDCs. Each BDC receives a copy of the domain's security accounts database and assists the PDC by sharing the load of authenticating domain logins. PDC and BDC computers always run the Windows NT Server operating system.
Other computers can be members of the domain. A member computer participates in domain security. It maintains its own local security accounts database and can authenticate local logins, but it can also accept login authentications of domain users that have been performed by the domain's PDC and BDCs. A computer running the Windows NT Server operating system can be a member server in the domain. A computer running the Windows NT Workstation operating system can be a member workstation in the domain.
Other types of computers–for example, Microsoft MS-DOS–based computers–do not store user accounts and do not participate in domain security. However, such computers usually have a default domain declared in order to support browsing of computer lists.
Microsoft SQL Server 6.0 is not recommended for installation on a PDC or a BDC, because those computers perform the resource-intensive tasks of maintaining and replicating the domain's security accounts database and performing network login authentications.
SQL Server will be installed on a computer running the Windows NT Server operating system, which in most instances will be acting as a member server in a domain. It can also be installed on a computer that is not a member of a domain, or even a computer that does not have any network capabilities.
Microsoft SQL Workstation 6.0 can be installed on a computer running the Microsoft Windows NT Workstation operating system. Microsoft SQL Workstation 6.0 has the same capabilities as Microsoft SQL Server, except that it is a single-user licensed product that supports a maximum of 15 simultaneous database connections.
When SQL Server is configured for security integration with Windows NT, it takes advantage of the security capabilities of Windows NT. Windows NT users can be authorized to log into the SQL Server. Windows NT user accounts can be mapped to login IDs. This allows a user to connect to and log in to a SQL Server without supplying a separate login ID or password. The user's original login to Windows NT is enough to allow (or, if appropriate, deny) access to SQL Server. With security integration, users maintain one login ID and password for both Windows NT and SQL Server.
With security integration, database-level security is still managed by the database owner. Database groups and users are created as for any SQL Server installation, and object and statement permissions are assigned in the normal fashion.
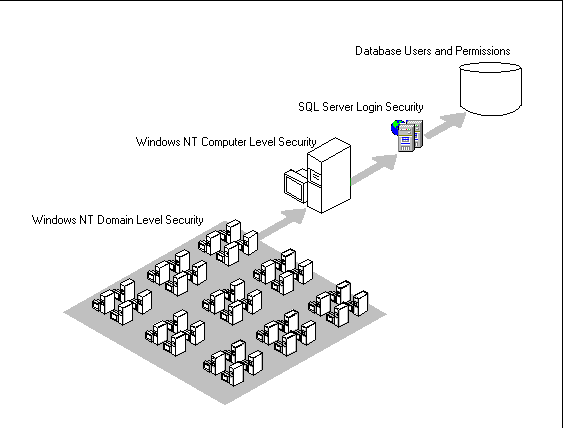
The following illustration shows that separate but interrelated security elements exist at the domain, computer, SQL Server, and database levels.

There can be more than one Windows NT domain in a network or enterprise. Trust relationships are security agreements between domains. These agreements enable pass-through user login authentication. Trust relationships and pass-through authentication allow a user to have only one user account in one domain, yet access the entire network.
When two domains are set up to trust each other, a user from one domain can be allowed (or denied) access to resources and actions for the computers of the other domain. The trusting domain accepts as valid the login authentications it receives from the trusted domain–in much the same way that a member computer of a domain accepts as valid the login authentications it receives from the PDCs and BDCs of its own domain.
For more information about Windows NT domains and security, see your documentation for Windows NT. For more information about security integration, see About the Server Login Security Mode. For more information about allowing a Windows NT user access to a SQL Server, see About Server Login IDs. For more information about allowing any user access to a database, see About Database Users.